Talking about the cyber threat, whether in companies or with individuals, is too often a challenge because of its intangible nature, which makes it difficult to perceive for a neophyte. Cyberattacks such as ransomware or other phishing are real for everyone, but the ways to protect yourself from them often remain obscure. A pragmatic approach consists in categorizing the surfaces of exposure, which favor the implementation of these threats.
- Human risks and their associated uses are by far the main risk in cybersecurity. It is usual to say that the solution to cyber problems often lies between the chair and the keyboard.
- A second category relates to the technical architecture of the data and the applications that handle it. Applications are increasingly switching to the cloud for questions of usage mobility and interconnection with third-party services.
- Finally, networks and associated configurations constitute the last category. The challenge here is to make data easily accessible to users and third-party applications without exposing systems to cyber threats.
The cloud comes to upset all of these subjects both from the point of view of the cyber attacker and for those who try to protect from it.
An architecture designed around internal uses
In the early 2000s, the norm for IT departments that had the means to do so, was to concentrate their core business in their own server room in order to control the architecture and operating costs. To understand the impacts, it is necessary to recall a few elements of context.
Digitization initiated a revolution in uses with the advent of Google solutions and the democratization of social networks such as Facebook or Linkedin. However, professional IT remained centered around large ERPs such as SAP and inter-application exchanges remained essentially within the company’s network.
Guaranteeing operational continuity by making the information system more reliable prevailed over a cyber threat, which was less significant than today. Business continuity and disaster recovery plans were therefore essentially focused on internal infrastructures. Cybersecurity focused on external threats, particularly with the new uses of web 2.0. CIOs were convinced of controlling their security within their network via security measures such as:
- External exposure limited to the DMZ (demilitarized zone of the network allowing to choose which application are accessible on the Internet).
- Network segmentation isolating servers by use (ERP, accounting, messaging, etc.)
- An EDR (Endpoint Detection Response) with an agent deployed on each server to detect threats and if necessary to remedy them by isolating the server from the network for example.
These few measures, far from constituting a comprehensive panel, are nevertheless representative of the securing of an internal perimeter by CIOs. The use of the cloud has reshuffled these cards to a great extent.
Digital transformation as a openness factor
The opening of information system to the outside took place under the pressure of digital transformation. Whether web portals (allowing content sharing or eCommerce) or the rise of CRMs such as Salesforce have led to the design of exchange gateways between the company’s internal network and these external services. Now the DMZs, although still necessary, are no longer sufficient to meet the needs. APIs manager have taken over to expose and consume more application flows, which are more functionally complex and require more granular security measures (with roles and usage profiles in particular).
At the same time with this hybridization of exchanges between internal and external solutions, data has become one of a company’s key assets. Quite naturally, cyber attacks have followed this trend by becoming more complex and encrypting this asset via ransomware.
Interestingly, ransomware has forced CIOs to adapt. Network modernization projects to prevent risks (for example by micro-segmenting inter-application flows) turn out to be less costly than completely rebuilding a data center in the cloud following a damageful attack.
However, the trend remains the same. Applications are migrating to the cloud and with them, security issues. EDRs must adapt to the proliferation of associated technical architectures, thus reducing the effectiveness of their protection.
The cloud, a new paradigm for cybersecurity
Behind this vague definition of application cloud hides an amalgamation of several concepts that need to be clarified.
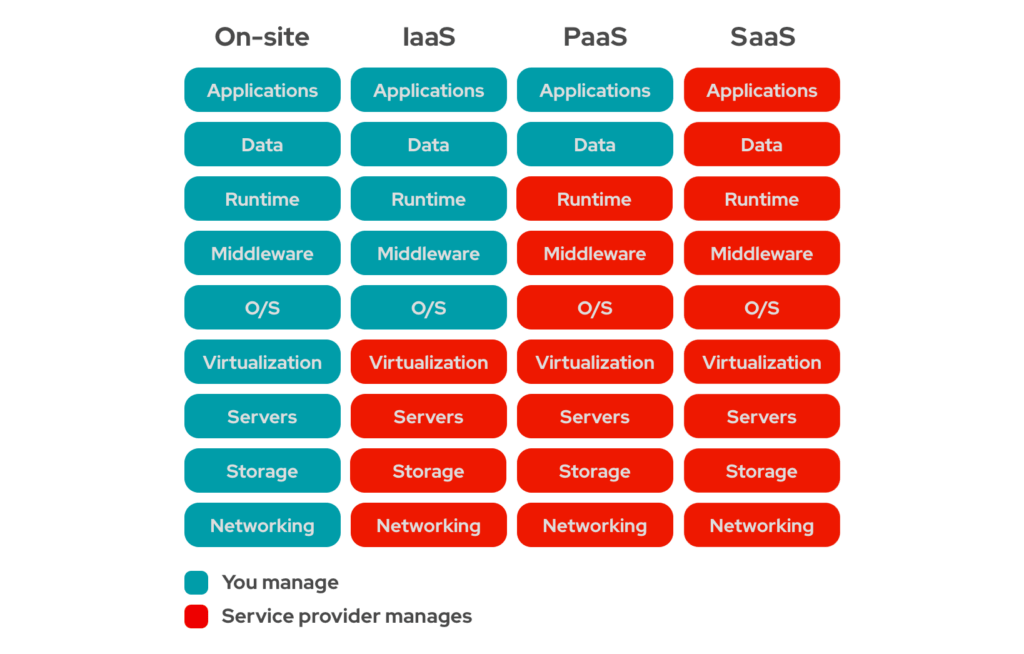
- IaaS (Infrastructure as a Code) is the most technically permissive service offering. Indeed, the service provider provides a server with a minimum configuration accessible remotely. The software layer is often reduced to a simple operating system accessible as an administrator. The user is then free to install the applications and configure them as he wishes.
- PaaS (Platform as a Service) is a less flexible service offer than the previous one. It offers a pre-packaged service to facilitate the installation of final software. This saves the end user from wasting time on repetitive configurations that he would have less control over in order to focus on his core business: the application solution he wishes to offer to end users.
- SaaS (Software as a Service) is the least flexible offer but also the most visible to the general public. When we talk about services like Linkedin or Facebook, we are not thinking in terms of technical architecture and data flow (to the great displeasure of cybersecurity) but directly in terms of the “service provided” to users.
The reality of the cloud is therefore protean but its common point is to have industrialized the deployment of the required instances (whether it is a container hosting a virtual machine, an application server or directly a ready-to-use service) via what is called infrastructure as a code.
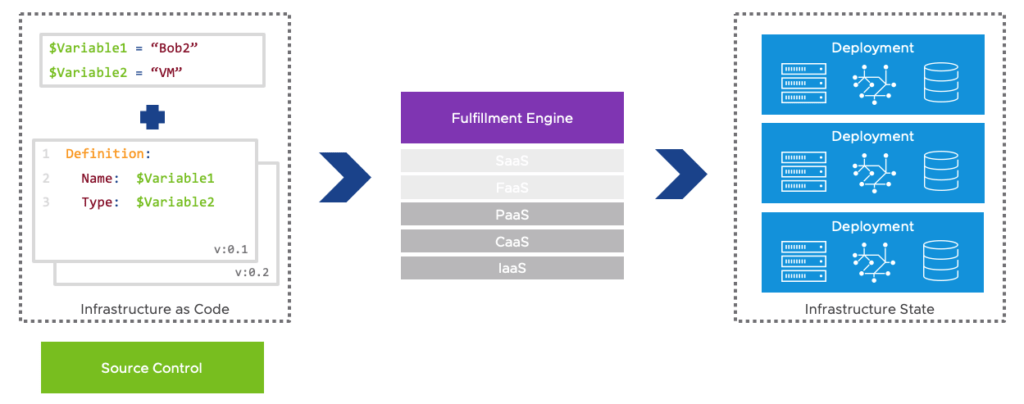
The infrastructure as a code allows via a tool such as Terraform to instantiate virtual machines or clusters of servers almost instantly. Ansible then takes over to configure the instance by deploying, for example, a ready-to-use server configuration.
Therefore, when a security incident occurs, it becomes easier to replace the compromised instance with a new secure instance, rather than patching the existing one that is compromised. The unavailability period for end users is thus shortened.
Towards anticipatory security
The paradigm shift between a locally administered data center and instances in the cloud is redefining the way to secure an information system.
The presence of infrastructure as a code makes technical audits easier to automate. The concept of “Cloud Security Posture Management” (CSPM) clearly describes the importance for a cloud to secure itself by systematically updating its components and libraries, avoiding disproportionately exposing network interfaces, finely managing user roles and permissions or avoiding leaving unencrypted passwords in the code.
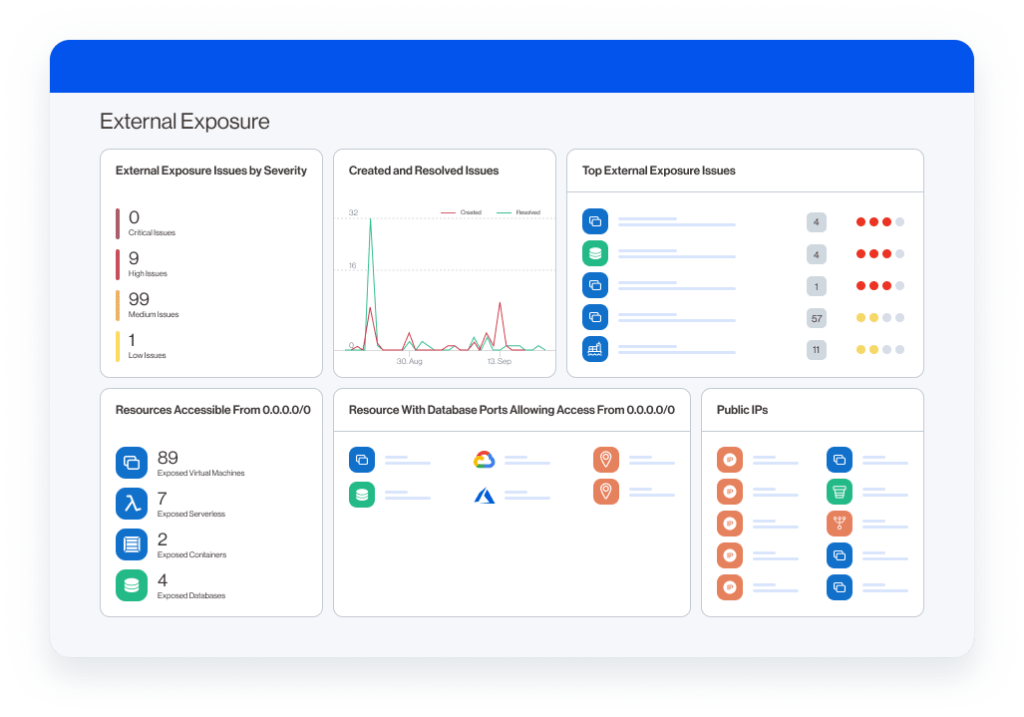
Can we therefore consider that the “traditional” approach to securing servers has been swept away by the cloud ? Nothing is less certain.
Admittedly, the ability to easily audit the instances that make up an application cloud is appealing. In particular, it makes it possible to have a readable dashboard and therefore a seller with IT decision-makers. Which security manager has never dreamed of having the attack paths on his IS automatically correlated to his vulnerabilities as the Wiz.io solution below allows?
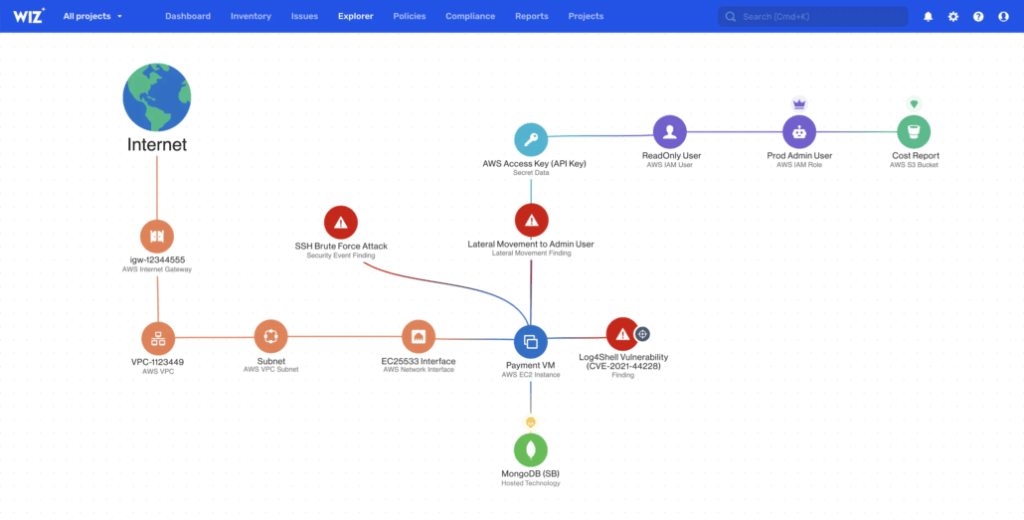
Beyond these more or less healthy aspirations, this type of solution is not intended to replace the traditional threat remediation services offered by classic EDRs. However, they greatly improve the cloud monitoring, which due to their ease of creation, do not encourage good cyber practices. How many times has a server instance been created in the cloud for a one-time prototyping need without being destroyed afterwards ? This very widespread drift is in particular at the origin of the business of “finops” which aim to rationalize the use of instances in the cloud and therefore to manage their costs.
In summary
There would still be many things to say about cybersecurity in the cloud. The challenge here is less to be exhaustive than to understand the underlying mechanisms that govern cloud security. The infrastructure as a code has promoted the reproducibility of instances as well as its compliance with best practices. Rather than securing a compromised instance, the cloud favors replacing it with a new secure instance. This ease of creation through evermore intuitive processes should not, however, hide the other side of the coin. The instances created must be managed throughout their lifecycle to be modernized and adapt to changes in the IS. This is the main question that the concept of cloud security posture management answers. The costs engendered by the cloud require thinking about its uses upstream. However, the resilience it offers in terms of cybersecurity as well as business challenges make it an essential element of the information system of tomorrow.
Don’t judge me by my success, judge me by how many times I fell and got back up again.
Nelson Mandela
