Unlike the reflections on cybersecurity decorrelated from the field that your author courageously writes in full view of all, putting it into practice is always trickier. In a field where many people pride themselves on their expertise, the demonstration of skills regularly borders on illegality. Certainly there are cybersecurity learning and challenge platforms such as the excellent Root-me.org. I will probably come back to this subject, which is an endless playing field. However fun they may be, these platforms do not allow you to test an entire information system.
This is why virtual machines exist, allowing you to emulate a complete system on your computer. Whatever your operating system and as long as you have a powerful enough machine, you will be able to emulate a third-party operating system on your PC.

Like a modern-day Janus, you will be able to act as an attacker and thus simulate exploitations of flaw without fear of the wrath of justice.
Metasploitable, the pre-packaged virtual machine for hackers
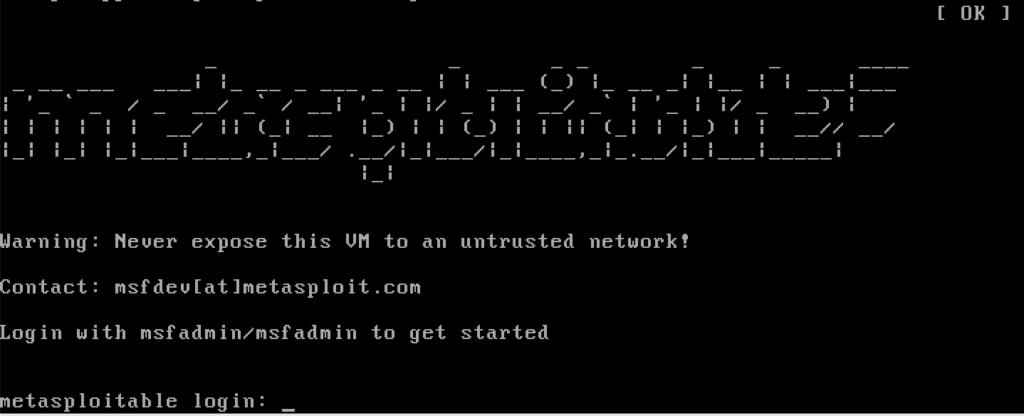
It is common knowledge that computer scientists hate to redo the same operation several times. Whether the primary reason is laziness or an unreasonable desire for automation matters little. I invite you to dive into the wonderful world of Metasploitable, a virtual machine designed around a particularly vulnerable system as a playground for hackers wishing to cut their teeth.
Originally Metasploit is an open source project whose aim is to provide information on vulnerabilities of computer systems, to assist in the penetration and development of signatures for intrusion detection systems (IDS, Intrusion Detection System ). Its parent company therefore created the Metasploitable virtual machine in order to allow its solution to be tested in complete security.
Below is a quick tutorial to install Metasploitable.
These few steps should get you up and running quickly without putting too much risk on your source system.
How to scan your own virtual machine?
Since this article is decidedly unlike the others, I attach below the excellent tutorial from Fengwei Zhang for scanning Metasploitable2 from a Kali Linux instance. This will allow novices to easily dive into the world of vulnerability recognition and detection in complete safety.
How to configure the network of your virtual machine?
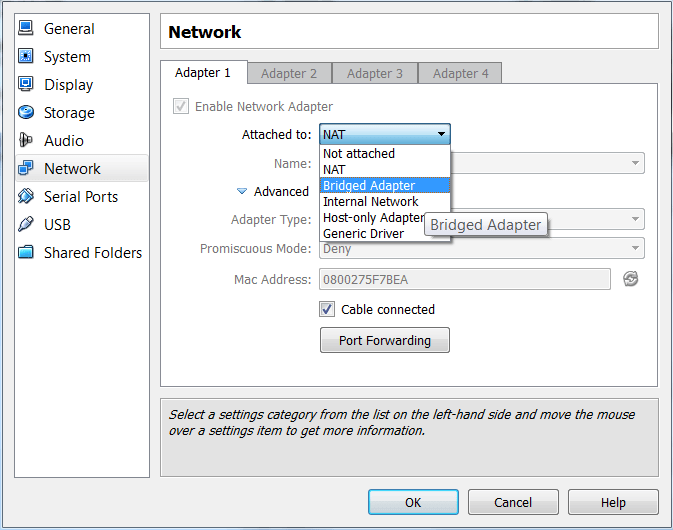
If like me, you tried to scan the Metasploitable instance from another virtual machine such as a Kali Linux VM for example, you realized that Metasploitable was not “visible” on the network. A clarification of the network configurations of virtual machines is required.

So we understand that the virtual machine must be configured for bridged access if we want to be able to scan its ports.
Are virtual machines the panacea?
A recurring criticism of the existence of pre-packaged virtual machines is that they themselves can contain threats within them.
Indeed, antivirus scanners can not easily scan for threats inside virtual machines.
At first glance, you might think that it would be a trivial question for antivirus and antispyware to check what’s going on inside a VM. After all, the guest virtual machine lives inside the host machine.
Unfortunately, this is far from the case. Part of the virtualization process involves slicing up data, making it more difficult to find the signatures of antivirus threats. Antivirus software look at two areas for malicious code: memory and file systems.
As a preamble, remember that most modern operating systems have a virtual memory system that divides the data inside the machine, the memory structures. Using multiple tables, virtual memory is then mapped to physical hardware storage addresses (hard drive etc.)
Memory structures make every program on the machine believe that there is a huge amount of memory when physical RAM is in fact limited. Modern operating systems support virtual memory by exchanging data typically between RAM and hard drive.
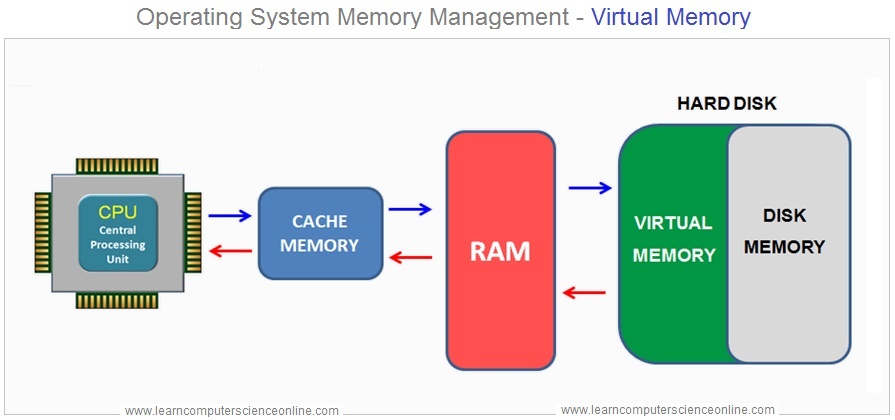
In a virtual machine environment, the guest has their own virtual memory system, as well as their own tables that map the memory view of various applications to physical memory. But the physical memory of the virtual machine is actually located inside the virtual memory of the host machine. This mapping is therefore a headache for the antivirus.
A similar problem occurs in the file system. In most virtual machine implementations, the guest file system is simply one large file in the host machine. All kinds of formatting information is stored in this file and all malicious files here are broken down into different pieces which are then distributed.
To scan the host machine, the antivirus can rely on the operating system to group hard drive sectors into files. But the anti-virus scanner doesn’t have that luxury inside the guest, where the guest’s file system breaks down the information into virtual sectors that are inside that big file on host’s hard drive.
There are ways to create antivirus scanners within a virtual machine.
Instead of looking for a series of signatures, the software would look for anomalies inside the guest. These anomalies could be more easily discerned by the host and do not require a full memory and file system mapping. As of this writing, if a virtual machine is contaminated, it will be difficult to guard against it.
The virtual machine, an essential tool for the hacker?
A quick comparison allows us to analyze the interest but also the limits of the use of virtual machines in terms of security.
Pros
- Use several operating systems on the same physical machine.
- Build a software architecture different from the physical architecture, notably with several machines that can communicate with each other.
- The creation of a virtual machine is based on a virtual hard disk. If the virtual machine crashes, the physical machine and the host system are not impacted.
- In terms of security, if you want to test software compromised by a virus, the virtual machine will limit the effects to the virtual hard disk (in most cases …)
Cons
- Virtual machines are less powerful than host systems because they access the hardware layer through an intermediary layer.
- If the host system is contaminated with a virus, the virtual machine may be compromised as well.
- The configuration of virtual machines, particularly in terms of rights and authorizations, can be complex.
Far from the clichés criticizing the relevance of using existing VMs and as long as we know their limits beforehand, virtual machines are currently an essential tool for carrying out cybersecurity tests.
“We all live every day in virtual environments, defined by our ideas.”
Michael Crichton