Hardly a day goes by without another cyberattack hitting the headlines with alarming messages and sensational numbers. Far from an ethical vision to democratize information, cybercriminals target both individuals and large multinationals. In France, February 2021 was marked by two attacks on hospitals via Ramsomware. In this context of a global pandemic, the immorality of these attacks caused a deep stir, forcing French President Emmanuel Macron to retaliate by significantly strengthening the country’s cyber defense means. Behind this announcement effect, it is interesting to look at the figures in order to better understand the reality of cyber attacks.
What are the motivations of the attackers and their typical profiles? How did they get into information systems, but also how are they discovered ? And finally, how to manage crises and anticipate these events ? These are all questions that we will try to answer below with the help of the benchmark of the Wavestone company, to promote cybersecurity in Europe.
What profile for the hacker in 2020?
From September 2019 to August 2020, the Wavestone study recorded an increase of more than 50% of major incidents reported by companies. If the myth of the lone hacker, the little computer genius is persistant (mainly because of the cinema), the reality of the facts is however different.

The diagram above can be read as follows:
- Mafia groups (organized and equipped) developing their own offensive tools are now the main scourge with 30% of attacks. Able to create high performing tools, they continuously improve their techniques by learning from past failures to improve theirs next attacks and maximize their results.
- Cybercriminals alone come in second and use already existing hacking tools, which they modify according to their needs. They are often competent computer engineers but limited in terms of time and resources.
- Script kiddies represent computer novices using out-of-the-box solutions without understanding the underlying mechanisms.
- Unorganized groups, unlike mafia groups, use existing tools but are capable of developing an offensive methodology. They are often the antechamber of mafia groups.
- Finally, interns are a heterogeneous group of malicious collaborators in a company.
Beyond the profile of the attackers, the study also reveals the type of threat these attackers lead. While 58% of threats remain opportunistic and favor ease, the current trend shows the professionalization of attacks with 39% of targeted threats, that is, attackers are mandated with a clear objective. The attack vectors remain fairly classic:
- 25% of intrusions start with a phishing email received by a company employee.
- 20% of intrusions exploit a web vulnerability.
- 16% of intrusions exploit vulnerable access services, especially those hastily deployed during the health crisis.
These intrusions allow us to better understand the motives that push hackers to act.
What are the motivations for cyber attacks in 2020?
According to Interpol former chief Khoo Boon Hui, 80% of cybercrime in 2012 was linked to organized cross-border gangs and represented a financial cost (750 billion euros per year in Europe) greater than the combined costs of cocaine, marijuana and heroin trafficking. A little less than a decade later, the motivations haven’t really changed.
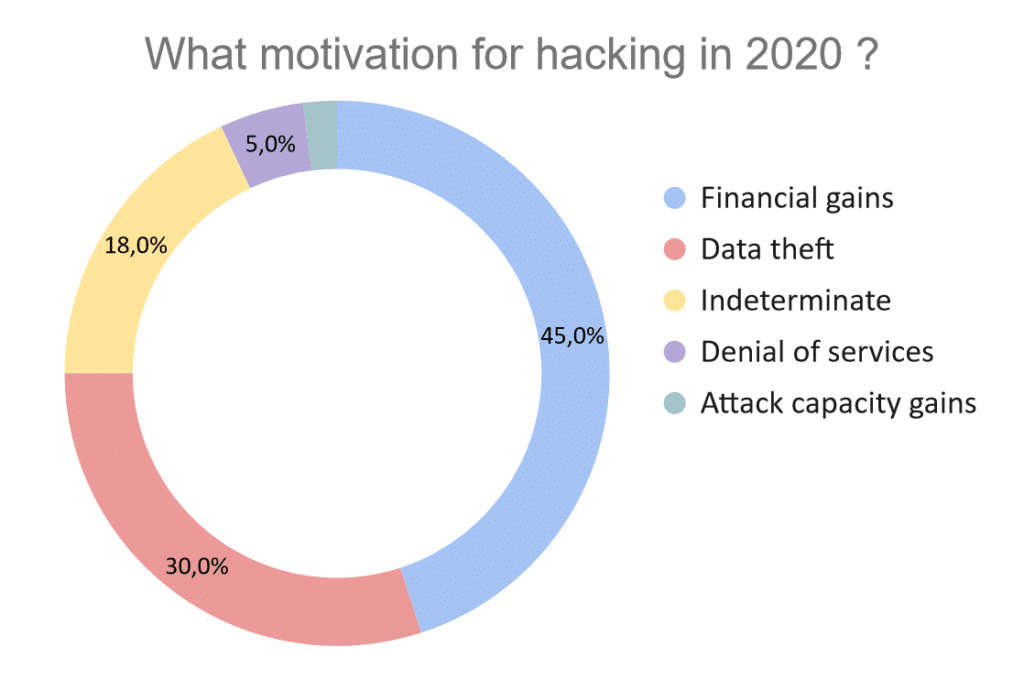
- Just under half of attacks are carried out without surprise for financial gain.
- 25% of attacks are carried out by ransomware, 18% are fraud and 1.5% are bitcoin miners
- Slightly less than a third of attacks are data theft (customer details, bank details, etc.)
The highlight of 2020 is the combination of ransomware + data theft which represents 10% of attacks.
- This was followed by indeterminate attacks (18%) – despite the compromise, the attacker’s motives could not be identified (attack abandoned etc.)
- 5% are volumetric attacks that often aim to make a service inaccessible
- Finally, 2% aims to gain in attack capacity (for example connected objects) to carry out attacks on other targets.
How are companies reacting?
Even though companies have realized the scale of the phenomenon, one figure testifies to the catching up that they must make to protect their infrastructures.
Less than 25% of major incidents were identified by company detection services.
Behind this seemingly disturbing figure hides a reality that is better than one might think: 94 days, the average time between an intrusion and its detection.
This period of approximately 3 months is compared to the 167 days (5.5 months) of delay in 2019. This reduction of more than 44% is mainly due to 2 factors:
- Detection services detect intrusions faster and have integrated the signatures of the most famous threats.
- Attackers have also adapted by exploiting compromised systems faster to avoid detection, even cutting corners on the attack surface or the information collected.
Does this mean the end of the ransomware wave? According to Fireeye’s predictions for 2021, nothing is less certain.
What prospects for 2021?
In his report on the security outlook for 2021, Fireeye points out that, like the health crisis that will continue into 2021, the wave of ransomware is expected to follow the same trend. It remains more than ever necessary for companies to anticipate these attacks by defining emergency plans, organizing simulation exercises or segmenting their networks.
Another fundamental trend is cyber espionage, which skilfully mixes state groups with mafias in the service of national interests (Russia, North Korea). These groups are responsible for missions outside their national territory and combine the collection of information with hacks whose objective is purely financial. In this globalized context, the migration of information systems to the cloud is at the forefront of cyber attacks. Stolen credentials, typically through phishing, exploiting poorly experienced business environment configuration and hacking vulnerable applications should be the classics of the year.
In summary, the year 2020 was marked by an increase in cyber attacks directly correlated with the global pandemic and the digitization of processes. About 2/3 of crises are due to ransomware, which combines the blocking of the information system with the theft of data, which is then often sold on specialized forums. This allows attackers to maximize their earnings in addition to a possible ransom payment. This practice was particularly tested in the United States with the Maze group before spreading around the world. 2021 is not set to escape its share of resounding attacks and cyber crises. However, companies are now aware of the threat. As information systems become stronger, attacks become more complex. The next few years should see the emergence of completely new offensive and defensive strategies.
“Some changes will seem negative to you on the surface, but you will quickly realize that this space is created in your life for something new to emerge.”
Eckhart Tolle
